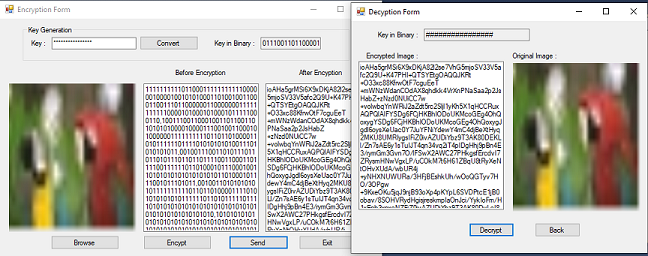
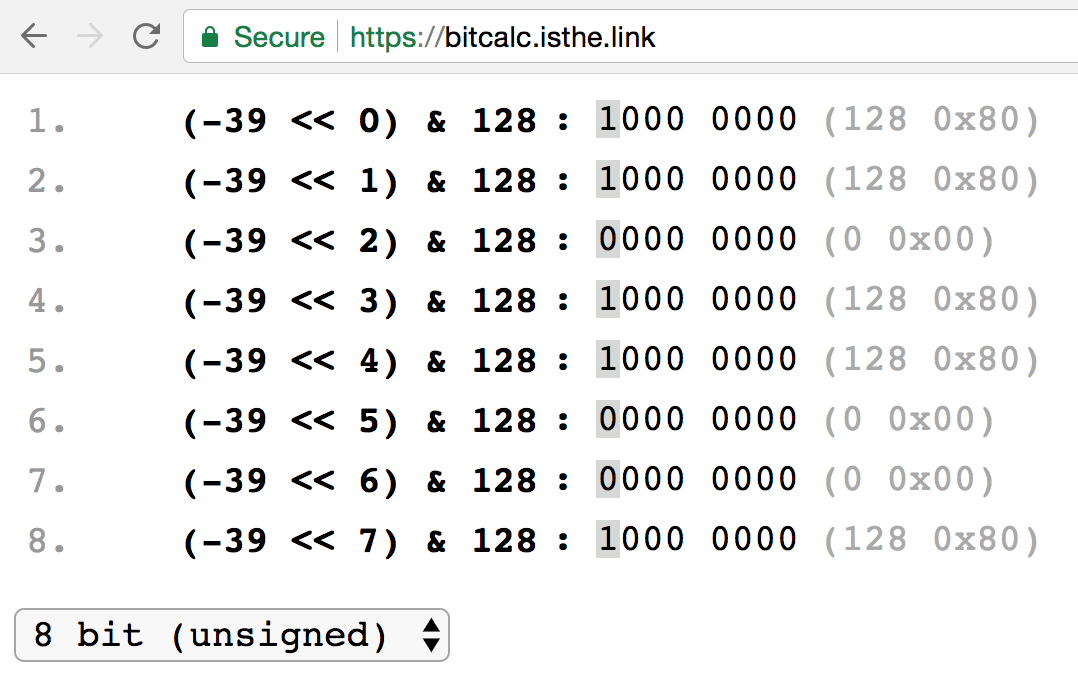
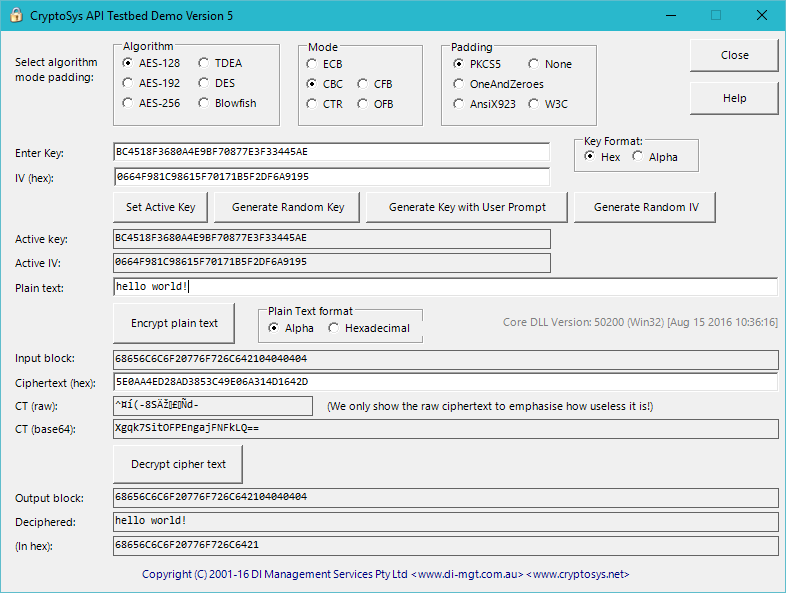
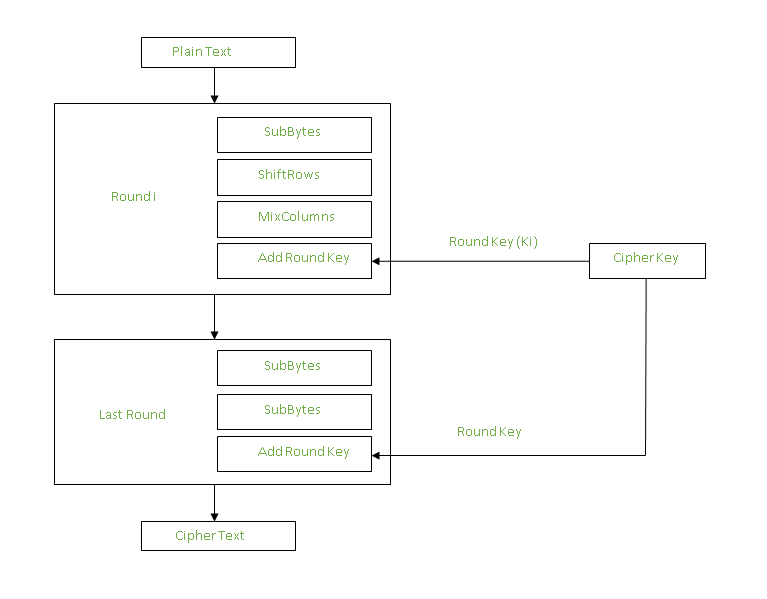
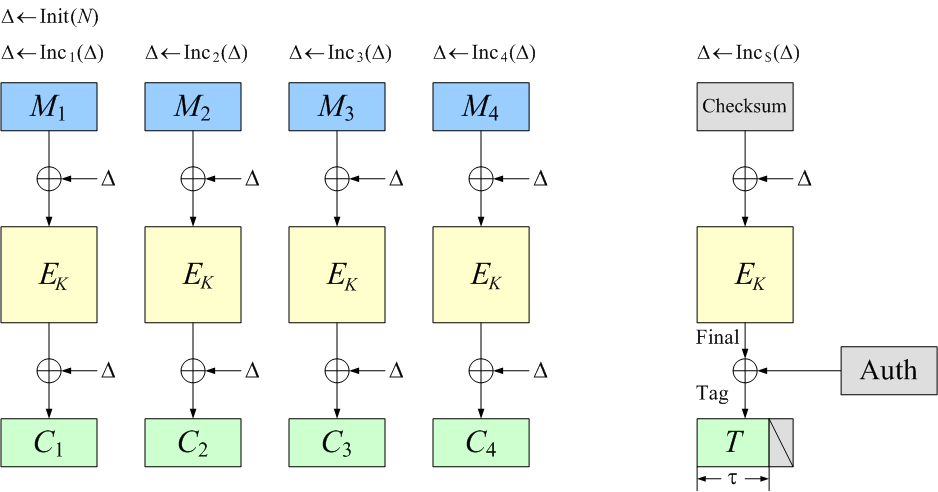
Encrypting Data with Golang. 3dfosi/gocrypt — A Golang Encryption… | by Jeremy Cheng | Level Up Coding

On the Properties of Bit String-Based Measures of Chemical Similarity | Journal of Chemical Information and Modeling
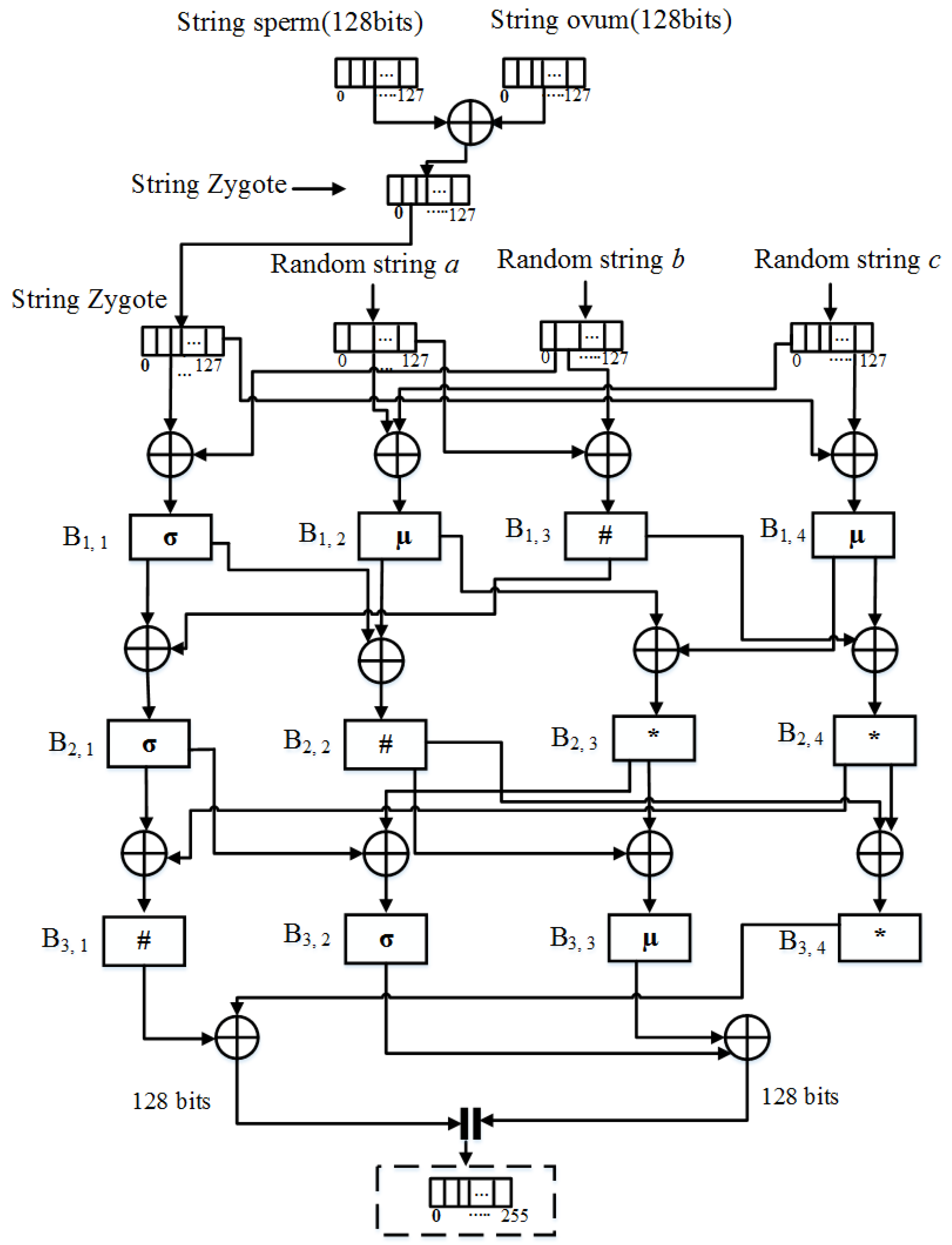
Applied Sciences | Free Full-Text | Omega Network Pseudorandom Key Generation Based on DNA Cryptography

Igor's Tip of the Week #128: Strings list - Malware Analysis - Malware Analysis, News and Indicators

8, 16, 32, 64 & 128-Bit Integer Limit | Processor & Data Types - Video & Lesson Transcript | Study.com
GitHub - joe-darkmatter/node-red-contrib-aes-128-cbc: A hex string-based 128 -bit AES with specifically CBC mode of operation ciphering algorithm for Node-Red module

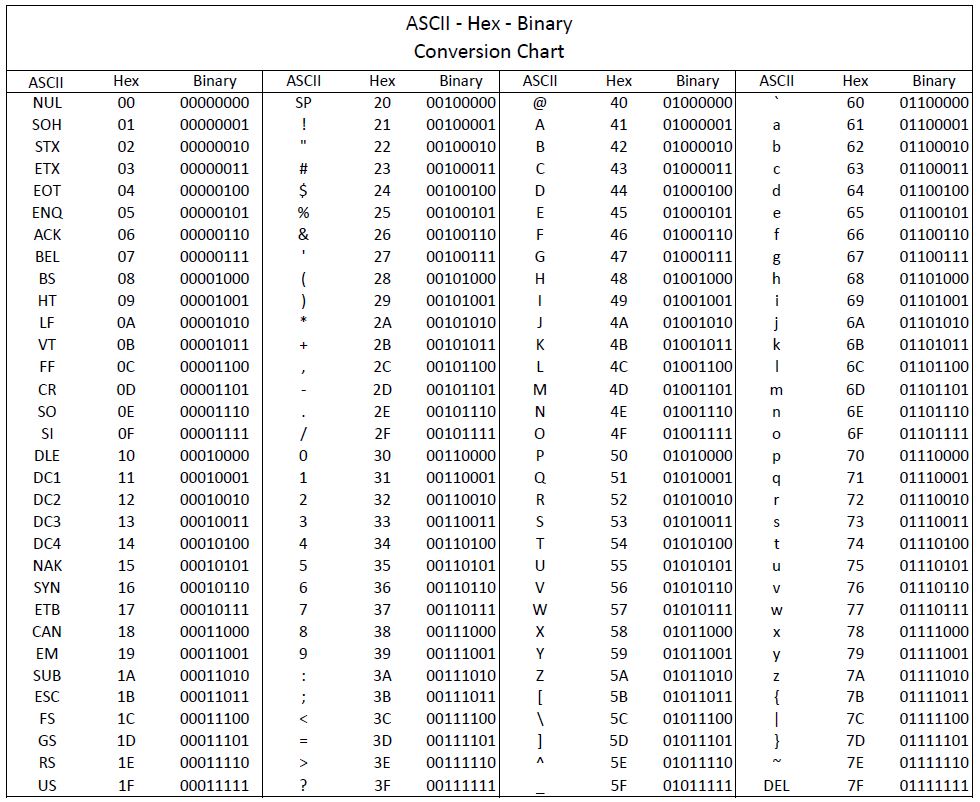
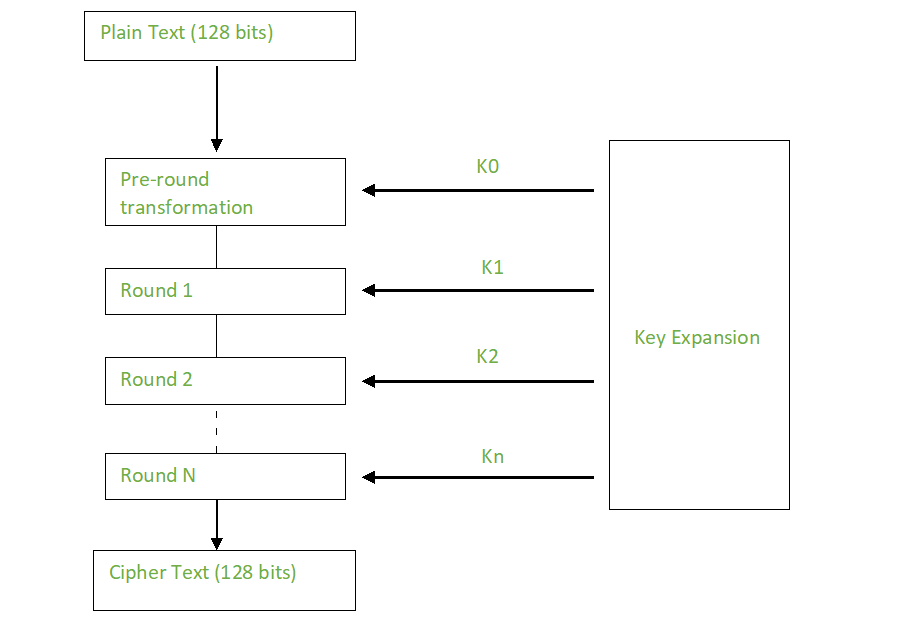
![java - String vs char[] - Stack Overflow java - String vs char[] - Stack Overflow](https://i.stack.imgur.com/WhEBr.png)